In Part 1, we covered the scope and limitations of the PCI CPoC standard. In this blog, we dive deep into building a CPoC solution in alignment with the standard.
The Solution Architecture:
As per the standard, a typical CPoC solution should include 3 major components
- a COTS device
- a CPOC mobile application and
- a back-end system to process the payment.
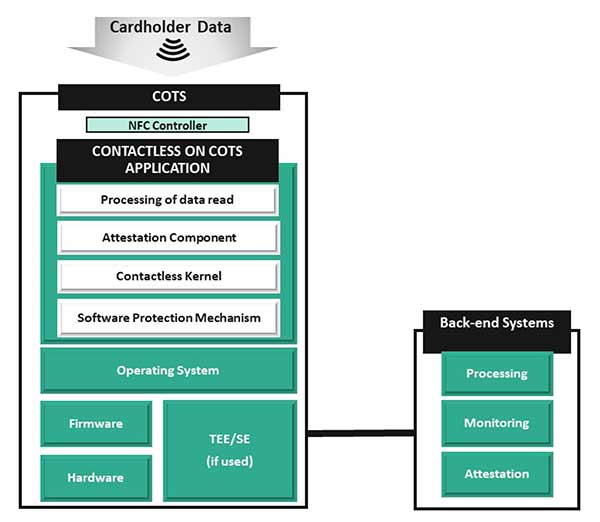
The solution architecture relies upon the following components to provide protection, attestation, detection, and response controls:
- A COTS device is the handheld device which is operated by a merchant to run the CPoC application. The COTS device may have a built in TEE (Trusted Execution Environment) to perform cryptographic operations, key management and ability to host trusted applications.
- A TEE is a tamper-resistant platform (typically a one-chip secure microcontroller) capable of securely hosting applications and maintaining the confidentiality and security of the data residing in it (e.g., key management and cryptographic controls).
-
A CPoC application resides in the COTS device and reads cardholder data using the embedded NFC interface in the COTS device.
A CPoc Application:
- Has an attestation component that performs attestation of the health-check data on the COTS platform and its CPoC application and passes that information to the back-end monitoring system.
- Contains software protection mechanisms to maintain its own integrity against attack vectors.
- Performs initial encryption of the payment and cardholder data and delivers the same through a secure channel to the back-end processing environment.
- Processes contactless transactions using a contactless kernel. The CPoC application selects kernel based on the characteristics of the transaction and the consumer device (e.g., credit card). The kernel contains interface routines, security and control functions, and logic to retrieve the necessary data from the payment card to complete a transaction as per the payment brands.
-
A set of back-end systems to carry out the following functions for the CPoC application:
- Attestation: Enforces agreed upon security policies on the COTS device, based opinion derived from the attestation of the health-check data.
- Monitoring: Monitors actual threats and attacks against the CPoC application and the COTS device. This system is built with security controls relating to detection, alert generation, and resolution.
- Processing: Processing system receives and processes the encrypted account data received from the CPoC application.
Transaction Flow in a CPoC Solution
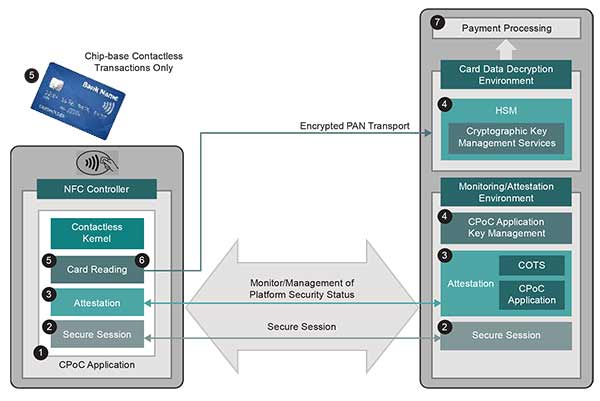
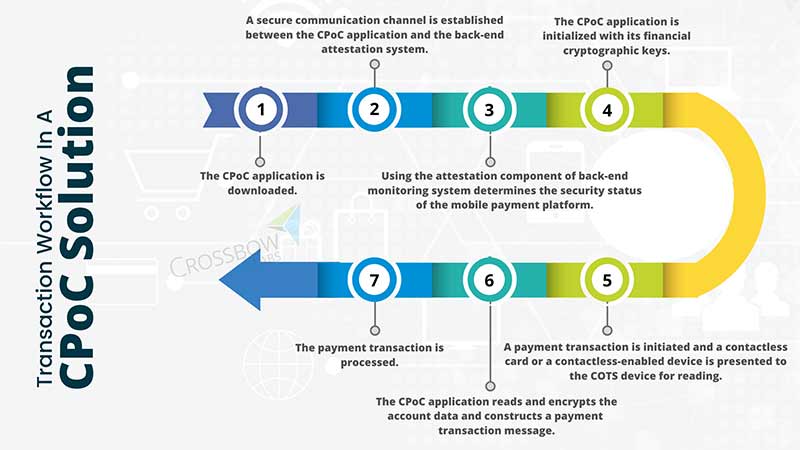
Overview of the requirements of the PCI CPoC Standard:
The standard has been divided into 5 requirement modules focusing on the 3 components of a CPoC solution – a COTS device, the underlying COTS Application and the back-end systems.
- Core Requirements – This module outlines the general security requirements that apply to the overall solution.
- Contactless Payments on COTS Application – This module outlines the CPoC application requirements that resides on the COTS device and its interface with other components of the CPoC solution.
-
Back-end systems – This module is split into two sub modules
- Monitoring and Attestation module outlines requirements for the back-end monitoring to detect to anomalies and fraudulent activities. This module also includes the necessary security controls and mitigation mechanisms for a COTS device for incident management and response.
- Processing module outlines the security requirements the system involved in payment processing and completion.
- Contactless Kernel – This module covers the card acceptance protocols and transactions protocols for EMV contactless cards and contactless magnetic stripe data (MSD) transactions.
Detailed analysis of each module and the mandatory requirements under each module will be discussed in the part 3 of this series.

